The world is changing, and cybercriminals’ adapting to these changes is quicker than the rate at which security solutions are developed. The progress of cybercriminals also contributes to the rise of cybercrime caused by technological developments.
To keep sensitive information safe, you must pay attention to tried-and-true methods. Firewalls and antivirus software are tried-and-true cyber security measures that need to update to keep up with the web’s ever-changing nature.
In this blog, let us understand what cyber resilience is. We will provide sufficient data and numbers to assist you in communicating its significance to other stakeholders within your business.
What is Cyber Resilience?
Cyber resilience is an organization’s capacity to maintain normal business operations, notwithstanding a cybersecurity breach or data loss.
Organizations face a wide variety of risks, and cyber attacks are only one. An automated command delivered during maintenance has the potential to knock all systems down, disrupting service.
Similarly, a human error or natural calamity might interrupt a company’s operations to the point that it cannot service its customers.
A cyber-resilient company can recover quickly from any interruption by drawing on a wide range of tools and strategies for keeping operations running smoothly.
The following are some of the instances in which your business might benefit from cyber resilience:
- The weakest element in your security strategy needs to improve with proper training. Keep your eyes open!
- The best way to secure your network is to stop attacks before they ever get in.
- The key to keeping people busy and your data safe is ensuring that all endpoints are protected against the current threats.
- The ability to recover from data breaches and other disasters with minimum downtime and minimal data loss makes automated backups essential.
How Does Cyber Resilience Work?
Cyber resilience operates by offering many layers of protection. There is no magic solution to deal with dangers that change all the time or to keep a business running smoothly if something unexpected happens. Defense-in-depth solutions solve the problem of infinite ways to attack and lose data because they don’t rely on a single solution.
Instead, businesses that practice defense in depth relies on a combination of technologies to secure their people, networks, and devices and quickly and easily restore any lost or stolen information.
The combined offerings of Carbonite and Webroot cover a wide range of preventative and recovery methods, allowing you to educate your staff, block attacks, secure your devices, back up your data, and recover quickly from failures.
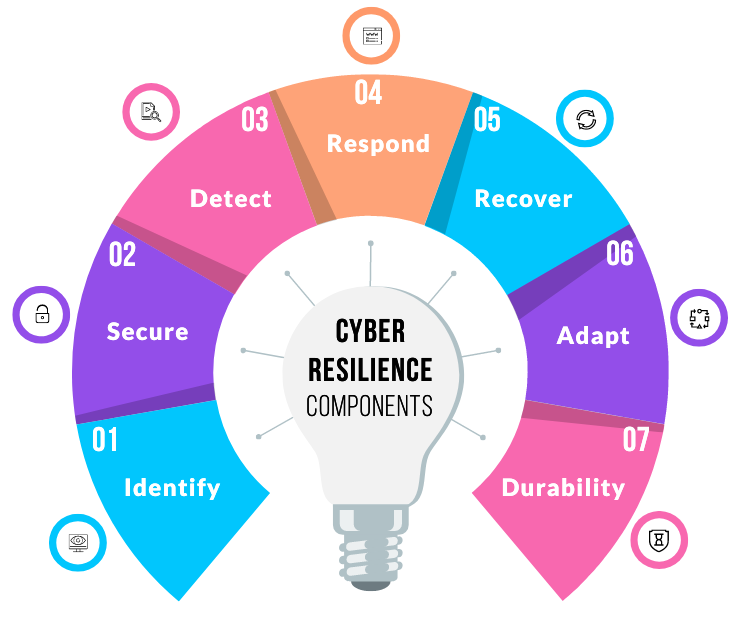
Cyber Resilience’s Components
Cyber resilience has several functions, such as safeguarding data, determining the origin of the threats, risk management, and effective functioning of the company during and after a cyber-attack. Cyber resilience enables the appropriate business continuation of a company even after a cyber-attack.
The response of an organization should be immediate, precise, and effective. This is why the following factors are considered while making plans to increase an organization’s cyber resilience:
Identify and Prepare
Identifying and making plans is the first step to being resilient. Taking an Asset Inventory is the first method of building resilience. Organizational assets should be recognized, including hardware, software, and physical infrastructure, to discover the vulnerabilities in these areas.
Analyzing the preparedness of existing internal and IT controls in the event of a cyber crisis is an integral part of this process, ensuring that security strategies are formulated in light of current risks.
In addition, it ensures that a company’s policies concerning data protection and security objectives are appropriately knitted with the IT infrastructure. The risks related to the company’s network security, the information inside the system, and the business’s IT infrastructure must be identified as part of this process.
Secure
After determining which assets and business processes are most at risk, the next step is efficiently deploying vulnerability assessment tools.
Businesses should undertake internal and external audits when evaluating the effectiveness of internal and IT security measures. In addition, all staff members need to educate on cyber security and their obligations during a cyber attack.
In this stage of the Cyber Resilience process, the information and systems are protected against cyber-attacks and access by unauthorized parties.
Information security policy implementation, employee education and training, and the upkeep of all hardware, software, and network components are part of this process.
Detect
The third level of Cyber Resilience needs continual monitoring of information and network systems to discover anomalies and possible cyber security incidents before they can cause significant harm.
The system is monitored for suspicious activities, such as unauthorized access, strange network traffic, malware attachments, and phishing emails. Advanced analytics can identify and examine hazards hidden inside or outside an organization.
Respond
The next step in building cyber resilience is to figure out what to do after a cyber crisis, like a data leak, has happened. Finding out what the fundamental issue is should be the first step in the immediate solution to the issue.
Afterward, it is necessary to identify the weakness that led to the cyberattack in the first place. The next step is to develop a good plan based on the weakness, the breach, and the information exposed.
Then, an effort should be made to reduce the damage caused by the breach by isolating the afflicted system or network.
In a data breach, the last step is to retrieve the missing information from any backups stored.
Recover
When a company is attacked online, its finances and reputation both suffer. It phase addresses post-data-breach recovery activities, as its name indicates. Since a quicker recovery means a more successful firm, resilience places a premium on it.
After identifying the affected systems or networks, the next step is to repair them, test them, and verify that they are working correctly before incorporating them into the cycle. This component of cyber resilience is focused on helping businesses bounce back quickly from monetary and image setbacks.
Adapt
During this process stage, employees are engaged in an in-depth conversation about the attack’s root cause and the appropriate responses.
The employees are provided with a clear image of the assault and how it will handle. The workers might see this as a kind of training, which can also serve as an incentive to defend themselves against any future assaults.
Durability
The effects of cybercrime are not limited to monetary loss and damaged credibility. A company’s resilience is tested by its response to a data breach. A company’s image can be damaged if sensitive consumer data is compromised. Therefore, it has to do better to win back customers’ confidence.
Spending money on solid security infrastructure and controls and performing frequent audits to ensure data privacy may help restore damaged reputations and win back customers. Restoration of the damaged systems and networks is necessary to improve the business’s infrastructure. An organization has to be resilient so that it can continue operating normally after a security compromise.
Cyber Resilience vs. Cybersecurity: What is The Difference?
The term “cybersecurity” refers to a component of “cyber resiliency,” which is itself composed of multiple subcomponents, including “security awareness training,” “endpoint security,” and “network security.”
These aspects constitute the more general concept we call “cybersecurity.” We can speak more generally about cyber resilience by including services like endpoint backup and recovery, backup for Microsoft 365, server backup, migration services, and more.
Cyber resilience is the state that results when data security, data backup and recovery, and keeping your organization online all work together.
Why is It Important?
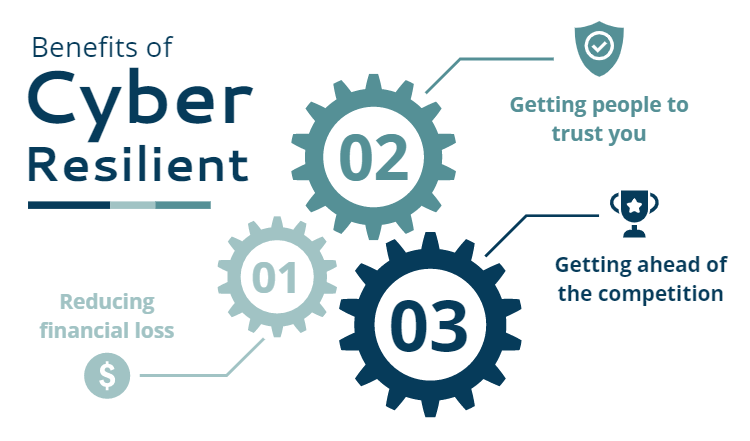
Maintaining operations in the face of cyber threats requires a solid action plan. Besides improving an organization’s security and reducing the probability of attacks on its most vulnerable systems, it also brings other advantages.
Reducing monetary loss and reputational harm is another benefit of cyber resilience. Additionally, a company’s consumers and clients will have more faith in it if it has been certified as a cyber-resilient.
Cyber-resilient businesses can also better maximize the value they provide to their clients, giving them a leg up in the market.
Reducing financial loss
If the business lost money, investors, stockholders, workers, and customers might all lose faith in it. IBM Security’s 2020 Cyber Resilient Organization Report found that over half of all businesses had a significant IT or business process disruption due to a cyberattack.
Getting people to trust you
Some businesses seek to win over clients by adhering to international management standards like the International Organization for Standardization’s ISO/IEC 27001. This standard explains what ISO/IEC 27001 needs from an ISMS to protect assets like employee records, financial data, intellectual property, and data given by third parties. In the United States, businesses can get PCI-DSS certification to accept payments like credit cards.
Getting ahead of the competition
Organizations that have built cyber resilience have a leg up on the competition. Best practices, like those in the Information Technology Infrastructure Library (ITIL), are the basis for businesses that work well. Likewise, they consider these while planning a management system for cyber resilience. In turn, this benefits the customers of such systems.
Final Thoughts
Cyber resilience, which is more than just cybersecurity, is essential in an increasingly challenging online environment. Criminals are constantly adapting, and new forms of cybercrime have the potential to undermine even the most robust defenses.
Including cyber resilience within the security infrastructure is crucial to recover from cyberattacks more quickly and keep operations running normally.
Furthermore, businesses should consider investing in cyber resilience as their primary security strategy.
Jennysis Lajom is an IT graduate, a chemist, an eCommerce business owner, and a Korean drama fan. Her passion for digital marketing led her to a career in graphic design, editing, and social media marketing. She is also one of the resident SEO writers in the Softvire US and Softvire Australia.